WAN Architecture
Get robust, scalable, and easy-to-use management tools that can handle the complexity of your multiservice and packet voice network. WAN provides extensive, reliable, and scalable element management capabilities to help you rapidly de
Abstract-Effective user security awareness campaign can greatly enhance the information assurance posture of an organization. Information security includes organizational aspects, legal aspects, institutionalization and applications of best practices in addition to security technologies. User awareness represents a significant challenge in the security domain, with the human factor ultimately being the element that is exploited in a variety of attack scenarios. Information security awareness program is a critical component in any organizations strategy. In contrast to other information security awareness work which mostly explains methods and techniques for raising information security awareness, this paper discusses and evaluates the effectiveness of different information security awareness tools and techniques on the basis of psychological theories and models. Finally, it describes how to measure information security awareness in an organization and explains an information security campaign conducted by Al-Rajhi bank in the light of our proposed model.
Keywords: information security, awareness, effectiveness.
1. Introduction
Information is one of the resources that an organization is heavily dependent on. If the critical information of an organization is compromised, the organization can suffer serious consequences, i.e. in the form of loss of income, loss of customers’ trust and maybe legal action etc. Therefore, information should be protected and secured.
Information security awareness is about guaranteeing that all employees are aware of the rules and regulations regarding securing the information within organization. Information security awareness should therefore form an integral part of any organizations’ overall information security management plan.
Many organizations use readymade information security awareness tools developed by some of the international information security companies, whereas some organizations make their own awareness tools according to the needs of the organization.
By implementing information security awareness program it is not guaranteed that every audience have understood and obeyed the guidelines, therefore, it is necessary to measure how much a particular method is effective in fulfilling its purpose.
The rest of the paper is organized as follows: Section 2 explains related work, whereas Section 3 proposes a model on the basis of psychological theories to find out effectiveness of tools. Section 4 describes some information security awareness tools and evaluates their effectiveness on the basis of the proposed model and Section 5 compares the effectiveness of the methods. Section 6 is on information Security Awareness metrics. Section 7 is on Al-Rajhi bank case study and Section 8 finally concludes this paper.
2. Related Work
Kruger and Kearney developed a prototype model for measuring information security awareness in an international gold mining company [1]. They measured the effectiveness of information security awareness program on the basis of knowledge, attitude and behavior. However, their research lacks the study of the underlying theory of the model.
Hagen et al. conducted research by analyzing answers of research question from 87 information security managers in Norwegian organizations [3]. Albrechtsen et al. described ‘information security dialogue’ as an effective tool for increasing awareness, however, the study lacks the fact that how effective is their approach as compared to other approaches of awareness [4].
According to Levin and Klev for a successful organizational learning, and change and development employee’s participation and collective reflection are very important [5].
In order to increase awareness level, knowledge should be given to the audience as stated by Forcht, education is necessary for increasing user’s ethical awareness [11]. In addition, for the protection of critical information assets security education campaign helps changing manager’s and employee’s attitude and behavior [15].
Although research has been done in the area of information security awareness, however the literature lacks the study on the effectiveness of information security awareness methods on the basis of psychological theories and does not describe the underlying theory of these methods. Psychology is the science of mind and behavior. Social psychology has been used for many years for research in the area of education, learning and human behavior. In this paper we evaluate the effectiveness of each tool and technique on the basis of our proposed model which is the integration of KAB model [8] and Theory of Planned Behavior (TPB) [17].
If you need assistance with writing your essay, our professional essay writing service is here to help!
3. Research Design and Methodology
Information security awareness can be defined as the individual’s passive involvement and increased interest towards certain issues and it is considered one of the key components of consciousness-raising the other being action [10]. According to information security forum [7], information security awareness can be defined as the extent to which every member of staff understands the importance of information security, the levels of information security appropriate to the organization, their individual security responsibilities, and acts accordingly. Different researchers have defined information security awareness; however, this study is based on the definition done by Information Security Forum [7].
Many information security awareness interventions are based on Knowledge-Attitude-Behavior (KAB) model which mainly focuses on the knowledge aspect of the human being [8] [1]. According to KAB model, as knowledge accumulates in a relevant behavior, e.g., information security, health, environment, education etc., changes in attitude are initiated. It basically explains the role of knowledge in the behavior change and the accumulation of knowledge. Such accumulation of knowledge in KAB model leads to change in attitude and finally behavioral change. Research in health awareness [8] and environmental awareness [2] shows that knowledge can be integrated in other conceptual framework in order to understand the process of change, but increase in knowledge is not the ultimate factor of change in behavior. It means that more than one variable affect behavior.
Thus, the KAB model, by itself is not sufficient to bring change in attitude and behavior for long term. In order to understand the change in attitude and behavior and how a change in attitude leads to change in behavior we borrow the support of the Theory of Reasoned Action (TRA) or Theory of Planned Behavior (TPB) [17]. This theory explains relation between attitude and behavior and includes both the direct attitude-behavior path as well as an indirect attitude-intention-behavior path [9] [17].
According to the theory of planned behavior, the change in behavior depends on the intention of the person. There are two factors that influence intention. One factor is attitude and the other is subjective norms [9]. So the level of intention towards an action will be higher if the person has a more positive attitude and more of a subjective norm towards the behavior. The attitude is what the person likes or dislikes whereas subjective norm is the person’s belief what people think about him should be done. These two factors together cause intention which leads to change in behavior.
To evaluate the effectiveness of information security awareness interventions, we propose a five step stair model. These steps are knowledge, attitude, normative belief, intention and behavior, where knowledge is considered as the foundation pillar of the model. Our proposed model takes the Knowledge attribute from the KAB-model and attitude and social norms from the Theory of Planned Behavior to achieve the desired change in behavior. Table 1 lists three information security methods from formal and four from informal instruction methods [18] and shows their respective effectiveness in the form of 5 points likert scale, where 5 being most effective and 1 being less effective. In table 1 the tick or ‘x’ mark below each component indicates its presence or absence in the respective information security awareness campaign. The overall effectiveness of a campaign method can be found by counting the number of tick marks in the respective campaign method. The more a security awareness method contains elements from the model, the more it will be considered effective in raising the awareness level.
4. Effectiveness of Information Security Awareness Tools
As we have formulated that how to measure the effectiveness of information security awareness methods, now we will find out the effectiveness of the following methods one by one:
1) Educational Presentation
2) Email Messaging
3) Group Discussions
4) Newsletter Articles
5) Video Games
6) CBT
7) Posters
4.1 Educational Presentation:
Behavior change objectives refer to intended changes in audience’s actual behavior. Campaigns and behavior change objectives, together contribute to the overall program objective which refers to awareness. Education is often seen as the key to changing behavior.
Different types of awareness campaigns are based on different psychological theories that focus on different aspects of human psychology. Usually the education campaigns target the knowledge aspect of the human and it ignores the motive behind the human behavior. Knowledge is not the motive for the human information security behavior; however, the lack of knowledge is a barrier in developing a desired behavior.
In educational information security awareness campaigns information is provided to the audience. Therefore these campaigns are mere the source of transfer of information and knowledge from the presenter to the audience. For example, information
Figure 1: Five step ladder model for measuring information security awareness
security awareness presentations provide information regarding password management, email management, virus protection, and organization’s information security policies.
Although this is very useful information but increase in information does not lead to a change in behavior and awareness. Social norms which are more effective in causing intention are missing in presentation. In addition, these campaigns are cheap, but boring and ineffective.
Now comparing the components of presentation with our proposed model (figure 1), it is clear that information security awareness presentations are more informative and provides more knowledge, therefore they can change the attitude but due to the missing component of subjective norms the component of intention of the audience remains unchanged. Therefore the overall effectiveness of information security awareness presentation is 4 points as shown in table 1.
4.2 Email Messaging:
One type of campaign for information security awareness is email messaging. These messages disseminate useful information regarding phishing, social engineering, password management and information security incidents. This method is effective in providing security related information and hence increases information security knowledge of the recipient. However, reading email message does not mean the message has been understood and internalized. Therefore, this method is insufficient in changing the attitude of the employee as this is one way communication and may not catch the attention of the recipient.
Using email messaging for information security awareness is good in providing information and knowledge. This method catches attention and cannot change the behavior therefore effectiveness stops on the second step of the model (figure 1), i.e., the overall effect of this method in raising information
Table 1: Information security awareness methods effectiveness
security awareness is only 3 points as shown in table 1.
4.3 Group Dialogue:
One type of information security awareness intervention is an informal meeting in which there is no one way communication. In this meeting about 15-20 individuals of an organization participate and the participants take full advantage of sharing knowledge and experience [4]. Different information security key issues are picked one by one and discussed; all participants are given equal opportunity to explain his point of view. In addition, organization policy regarding information security is discussed.
Our academic experts are ready and waiting to assist with any writing project you may have. From simple essay plans, through to full dissertations, you can guarantee we have a service perfectly matched to your needs.
Participants are asked to describe any information security incident happened with them and whether those incidents were reported. The consequences of such security incidents are discussed among the participants. Such strategy of discussing incidents in workshops is good to motivate the participants. This strategy is based on the theory of reasoned action, which changes which is changing intention through attitude change and social norms. Group discussion involves participants in the group conversation that increases the information security related attention and intention of the participants [4]. Group discussion and meetings are more of interactive type and hence more effective.
This approach has been found useful in increasing the awareness level by the use of knowledge, attention, attitude, social norms, motivation and behavioral strategies. This approach uses social norms and interaction that influence individual understanding of information security.
In addition it is interactive and engages all the participants. Due to the environment participants know about information security attitudes of each other and therefore increases their motivation to adopt positive information security behavior. This method of intervention accumulates all components of our proposed model (figure 1) and therefore the overall effectiveness of information security related awareness related Group Dialogue is 5 points (see table1).
4.4 Articles in Newsletters:
Newsletter is a monthly or quarterly one to four pages information security report. These reports can be both in electronic or print format. They are distributed among the employees within organization and are designed with the aim to increase employee’s information security awareness. It has a company logo on it with the date on which the newsletter was issued. The newsletter discusses the new emerging threat, for example, newly discovered viruses, information security incidents and useful guidelines for information security. These newsletters are good in transferring information security knowledge.
However, it is not possible for the security managers to know whether the employees have read the newsletter and they have understood and internalized it or not.
Newsletters are also very informative and knowledgeable material due to which they are good in changing attitude towards information security awareness. However, it does not have the component of subjective norms, due to which it cannot change the reader’s intention and so behavior. The overall effectiveness of Information Security Newsletters, according to our proposed model is only 2 points.
4.5 Video Games:
Some information security awareness researchers have proposed the use of video games to increase information security awareness [2], [6]. This technique is also used by researchers in other disciplines to increase health [12] [13] and environment risk awareness [19] [20]. It is claimed by the researchers that video game is a good technique in motivating player towards adapting the desired behavior as it catches the player’s attention and engages him. However, this method does not have a component of knowledge transfer unless the player has already gained the information security knowledge before starting the game. In addition, it is related to information security in general and does not specifically reflect the policy of the organization or organization’s related security issues. In our proposed model, knowledge is the foundation pillar for the increasing information security awareness and behavior.
Video games are more interactive and keep the player engaged. They are beneficial in changing attitude; however, they are not a very good source of knowledge. Due to good source of motivation they can lead to a very limited change in behavior therefore the overall effectiveness of video game on one’s information security awareness is only 2 points.
4.6 CBT:
Computer based training has several advantages over conventional methods of information security awareness. CBT is available at all times to all employees within the organization and it is an effective method of information security awareness training. The employees of the organization can acquire the desired training at their own pace. However, CBT requires more resources and do not reflect the organization’s policies. They are readymade. In addition this method lacks the benefit of interaction between instructor and audience and among the audience. Therefore, a social norm which is one of the components of our proposed model is missing in this technique. Due to the missing component of social norms human’s information security intention and behavior does not change, therefore, the overall effectiveness of CBT is 2 (table 1).
4.7 Posters:
Posters are simple and effective reminders of information security that catches end user attention and reminds basic information security rules. Posters require fewer resources. Catchy slogans and attractive designs greatly contribute to the effectiveness of posters. In addition to the design and contents of the posters, location where the poster is displayed also attracts the attention of the viewer. Posters displayed in high traffic area are more likely catch the attention of the viewers.
However, relying on information security awareness posters alone is impractical as it is not possible to explain something on posters. In addition, a social norm which has a great contribution is missing in the posters. Due to the missing component of social norms, intention cannot be changed and therefore, information security related behavior remains unchanged. Hence the overall effectiveness of posters is only 2 as shown in table 1.
5. Comparative study of the effectiveness of information security awareness tools:
In the above section (section 4), the effectiveness of several information security awareness campaigns have been measured one by one. The overall effectiveness of each of them is shown in table 1. The most effective of them is information security related group discussion. It considers all components of the proposed model namely knowledge, attitude, social norms and intention. Information security awareness presentations are the second most effective method for increasing awareness as shown in figure 2. Email messaging is the third effective method whereas newsletters, video games, CBT and posters are fourth effective methods for increasing information security awareness.
6. Information Security Awareness Metrics:
According to NIST 800-50[15] and NIST 800-55[16], metrics is defined as tools to facilitate decision making, improve performance and accountability and help determine an organization’s IT security awareness and training. Information security managers need methods to measure the information security awareness level of employees of
Figure 2: Comparison of effectiveness of ISA tools
their organization. A thorough literature review is failed to provide a universally accepted and validated measure of information security awareness. In this section we present the methods to measure the information security awareness. These metrics are specific, measureable etc.
6.1 Security related helpdesk calls:
Information security awareness of employees can be measured by counting security related calls to helpdesk. However, the type of calls to the helpdesk varies and therefore every call to the helpdesk cannot be counted in the measurement of awareness. For example if the calls are for resetting the password to unlock the account then this is due to the ignorance of the user. But if an employee or customer calls helpdesk for the advice regarding choosing password then it is counted in measuring information security awareness level. The more the number of such calls to helpdesk the more the level of information security awareness in the organization.
6.2 Accesses to unauthorized online services:
Some organizations do not allow the use of certain online services which are not related to the organization’s business. With the use of automated tools it is possible to find out the number of attempts made to access those unauthorized services. Such measurement can be done on monthly or quarterly depending the information security management policy of the organization.
6.3 Accesses to information security intranet pages:
Many organizations create informative websites for the purpose of information security awareness training of the employees. Employees are instructed to visit those pages for the information security awareness training. The gradual increase in the number of hits to the website shows an increased interest of employees in information security awareness. The number of hits means the number of users being exposed to the information security awareness material.
6.4 Survey questionnaires based on knowledge:
A survey based on information security questionnaire can be conducted within the organization among the employees. Unlike other types of measure this survey assesses the knowledge of the employees about information security which indirectly measures the information security awareness level. Such includes question like, How to make a strong password? Is it secure to open an email from unknown sender? Do you leave the system unlocked while away from the desk? Or do you lock the system before leaving? Such type of survey has many advantages and gives a clear whether the employees have knowledge about information security. Thus an increase in the correct answers of the survey shows an increase level in information security awareness. Such survey can be conducted monthly or quarterly depending on the policy of the organization to measure the level of information security awareness within organization.
6.5 Phishing emails:
It is beneficial to find out the number of phishing emails that have been opened by the employees of the organization. The number of accessed phishing emails shows the level of information security awareness. The more is the number of phishing emails accessed, the less the level of awareness. Information security conscious users will less likely access suspected phishing emails. Such information can be collected either by asking employees whether they have received any phishing emails in a specified period of time or using an automated tool.
6.6 Security Incident Database:
Information security awareness can also be measured by counting the number of security incidents being reported. It also indicates the awareness of the user who knows who to contact when an information security incident occurs. Therefore, increase in the number of reported incidents as compared to the number of unreported incidents shows the increase level of information security awareness.
In addition to the above strategies, the statistics of increase and decrease in the number of Trojan horse attacks and analysis of log files of intrusion detection system can assist in measuring the information security awareness.
Table 2: Information Security Awareness metrics
7. Case Study: Survey of Information Security Awareness of online users of Al-Rajhi Bank:
Al-Rajhi bank is one of the largest banks in the kingdom of Saudi Arabia, founded in 1957. It has over one million customers including business customers. The number of employees working in Al-Rajhi bank is over 7,447. It has about 550 branches more than 2600 ATM’s, 16700 POS terminals installed with merchants and the largest customer base of any kind in the kingdom. Apart from Saudi Arabia, it has branches operating in Malaysia, Kuwait and Jordan.
Al-Rajhi bank uses latest information technology to provide better service to its customers. Like other banks and financial organizations, Al-Rajhi bank also faces internal and external threat in terms of customer’s identity theft. The management of Al-Rajhi bank agreed to assist us in the information security awareness program. The output of which was to find the effectiveness of two information security awareness raising methods.
8. Conclusion and future work
This research is a theoretical study of information security awareness based on the psychological theories of awareness and behavior. This study shows that psychological theories of education, learning, environmental and health behavioral change can be used to make information security awareness methods more effective. It further clarifies that the aim of many information security campaigns is to increase information security knowledge. Many post-campaign surveys ask questions focusing mainly on the knowledge of the participant and not behavior. Answering questions correctly does not mean that the user is motivated to behave according to the knowledge they gained during the campaign.
According to this study this is the actual behavior which, in fact, reflects the awareness of the end-users before and after the information security awareness program.
ploy and manage services. The high-performance carrier-class element and network management product is deployed worldwide in some of the largest service provider networks. It can operate as a standalone system or can be integrated as an element using its northbound interfaces for highly efficient flow-through operations
Enhanced operator workflow and usability simplify configuration, fault monitoring, and troubleshooting operations.
The enterprise business is changing as new types of payroll systems.. As the number of branches continues to increase, the reliable and secure delivery of these evolving services demands a network that can similarly evolve to meet these demands and enable business success.
IT professionals require higher network performance, scalability, availability, security, and service capabilities. The Branch-WAN payroll system architecture is developed to address these key areas of customer concerns. To meet these requirements, the Branch-WAN payroll system architecture features scalable and resilient network infrastructure, integrated security, wireless, and payroll system intelligence to provide seamless service capabilities that include Unified Communication, media collaboration, and data/Web 2.0.
Architecture
This is dedicated to delivering solutions that meet and exceed customers’ business and technology requirements by integrating best technologies, services, and platforms. The WAN Payroll system architecture is part of a comprehensive approach to providing an end-to-end enterprise network architecture. This model is known as Places in the Network architecture.
The architecture addresses the differing requirements for systems design and deployment in the three principal network areas: the campus, the data center, Internet edge, and the WAN. See Figure 1
Figure 1: Architecture
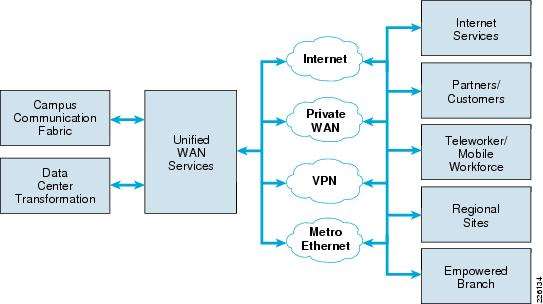
When discussing an enterprise network, it is important to consider that most networks are built from a discreet set of interconnected, architectural elements-each of which has its own requirements. A branch office, for example, may not have the same scalability requirements as a data center, but has a greater need for reduced form-factor devices with high-value integrated services.
The typical corporate campus network offers users high speed and secure network connectivity, Unified Communication services, wireless services, and access to corporate payroll systems and databases. A well-engineered network must offer workers at branch sites the same network services as campus workers, to maximize productivity and ensure business objectives are met. The Branch-WAN payroll system architecture offers an end-to- end system design that delivers a flexible, scalable, and secure network that supports advanced network services for branch office workers.
Figure 2: WAN Payroll system architecture (Frame work)
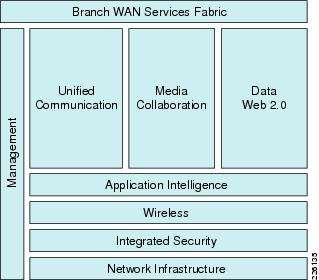
The WAN payroll system architecture shown in Figure 2 has the following layers:
• Network Infrastructure-The foundation that provides routing, switching, quality-of-service (QoS), high availability, and other functionalities to ensure that the network is scalable, flexible, and resilient.
Network Infrastructure-The foundation that provides routing, switching, quality-of-service (QoS), high availability, and other functionalities to ensure that the network is scalable, flexible, and resilient.
• Integrated Security-This layer extends the corporate security policy to the branch, providing network infrastructure protection, secure communication, threat mitigation, and network monitoring across both the Branch and WAN PINs.
Integrated Security-This layer extends the corporate security policy to the branch, providing network infrastructure protection, secure communication, threat mitigation, and network monitoring across both the Branch and WAN PINs.
• Wireless-this layer provides user network connectivity anywhere within the enterprise, giving employees greater flexibility, and increased productivity.
Wireless-this layer provides user network connectivity anywhere within the enterprise, giving employees greater flexibility, and increased productivity.
• Payroll system Intelligence-this layer provides various payroll system optimization techniques using optimization (i.e., TCP flow optimization, data redundancy elimination) and control for payroll system classification and prioritization using QoS. This optimizes use of the WAN bandwidth and, enables branch users to access the same payroll systems as campus users, with similar user experience.
Payroll system Intelligence-this layer provides various payroll system optimization techniques using optimization (i.e., TCP flow optimization, data redundancy elimination) and control for payroll system classification and prioritization using QoS. This optimizes use of the WAN bandwidth and, enables branch users to access the same payroll systems as campus users, with similar user experience.
• Management-this layer provides the ability to easily provision and monitor the network.
Management-this layer provides the ability to easily provision and monitor the network.
With these layers, it is imperative that unified communication (i.e., Unified Communication), Media Collaboration (i.e., Tele presence, IP Video Surveillance, Desktop Video, and Digital Media Systems), and Data Web 2.0 (i.e., collaboration payroll systems) work seamlessly across the Branch-WAN solution.
Technologies Considered
Types:
There are number of WAN technologies like point to point connection, circuit switching and packet switching. The WAN communication which is carried over a leased line is called point to point connection. In a point to point network the message from the customers end is traveled to the remote user via an ISP. Circuit switching is the data communication which is stared when there is need to communicate and it is terminated afterwards. It is like a telephone call. When the two users arte connected and identified, the data is transferred in other words voice is transferred. When the transmission of the data is complete the call is disconnected again. Packet switching data network is a WAN technology in which the network of the user is established in the carrier’s system. The examples of packet switching network include asynchronous transfer mode (ATM), switched multi megabyte data services (SMDS) and frame relay.
Optimization
The purpose of WAN optimization is to eliminate the flaws in the packet data transfer in shared WAN systems. There are many techniques of optimizing the WAN technology. These optimization techniques include duplication, compression, cashing, protocol spoofing, traffic shaping, equalizing, connection limits and simple rate limits. The process of duplication sends a reference of the actual data, this helps in preventing from data redundancy. In order to present data patterns in an efficient manner compression is used. The process of caching reduces the bandwidth up to 30%. The multiple requests are tied in one bundle using protocol spoofing. Traffic shaping controls the amount of data handling and also monitors and guides the data traffic. When the data is sent according to the priority of the data usage it is known as equalizing. Connection limit averts from the access grid locks in access points and routers due to the lack of service or peer to peer connection. Simple rate limits the users from getting more than the data which has been fixed for their use. The purport of WAN optimization is to overcome the difficulties such as expensive bandwidth and to decrease the user’s experience time. The scalability of WAN is nowadays an important consideration and hence WAN optimization is used to target such issues as well.
The typical small branch design includes a 1.5 Mbps Ethernet private WAN connection. The router terminates the VPN and routing from the central site and implements QoS policy. The router also hosts the following integrated services:
• Security (Firewall, IPS)
Security (Firewall, IPS)
• Unified Communications (SRST, FXO / FXS ports)
Unified Communications (SRST, FXO / FXS ports)
• Payroll system intelligence
Payroll system intelligence
The branch also includes a Layer-2 access switch with the following key features:
• Power-over-Ethernet (PoE)
Power-over-Ethernet (PoE)
• DHCP snooping
DHCP snooping
• Spanning tree
Spanning tree
• Class-of-Service (CoS) on access ports
Class-of-Service (CoS) on access ports
• QoS
QoS
• Port security
Port security
• Dynamic Address Repayroll system architecture Protocol (ARP) Inspection
Dynamic Address Repayroll system architecture Protocol (ARP) Inspection
Wireless LAN may be implemented with a router module or standalone controller/switch.
New Issues
- The key to an effective next-generation WAN architecture? Match technologies and services to interconnection requirements. Herewith a blueprint:
- Data center-to-data center connectivity: Data center interconnectivity requires high-capacity, low latency links. Although multiprotocol label-switching (MPLS) can do the trick, it’s often an expensive solution. Telecom architects are increasingly turning to solutions such as carrier Ethernet (either point-to-point or virtual private LAN service, VPLS), or dark fiber or wavelength services. Seventy-one percent of organizations will be deploying some form of carrier Ethernet by the end of 2010, typically for data center-to-data center connectivity.
- Why? Three reasons: First is cost. On a per-megabit-per-second basis, carrier Ethernet can run 25% to 50% lower than other technologies. Second is bandwidth: with Carrier Ethernet, users are able to procure up to 10Gbps of bandwidth (the equivalent of 2.5 OC-768 circuits). As a result, as bandwidth requirements increase, carrier Ethernet becomes more appealing. Finally, there’s the ease of deployment and management. Users report that carrier Ethernet is straightforward to install, and performs reliably. “Right off the bat, it worked like a charm,” says the CIO of a midsized professional services firm.
- Data center-to-branch, and branch-to-branch, connectivity: Most organizations (80%) have deployed MPLS, and plan to continue using it for site-to-site connectivity (at least for midsized-to-large sites). Some firms – mostly leading-edge organizations – are also looking at rolling out carrier Ethernet for the “core” WAN. The primary challenge? Availability. Carrier Ethernet isn’t as widely-available as MPLS.
- Remote-site and micro branch connectivity: For smaller sites, companies are exploring a range of connectivity options. An Internet VPN is one approach (and one that’s increasingly common). A more innovative approach is to deploy 4G wireless technologies, either direct to the router or to each individual employee. Again, the challenge here is availability: Most carriers are just beginning to roll out broadband wireless (in the U.S. at least). Another problem is capacity: Carriers haven’t designed their networks for use as wired-WAN replacements.
References:
en.wikipedia.org/wiki/Application_architecture
apparchguide.codeplex.com/
www.amazon.com/Patterns…Application-Architecture…/0321127420

 Effective Next Geeffectiveness Of Information Security Awareness Information Technology Essayneration Wan Architecture
Effective Next Geeffectiveness Of Information Security Awareness Information Technology Essayneration Wan Architecture