WORD PROCESSING: AN INTRODUCTION
Outsourcing problems are very complex where even a small decision when taken wrongly can lead to unpredictable risks. From JIT’s outsourcing experience, the following questions should be considered in order to analyse the case.
How to strategically select the appropriate activities that can be outsourced or be maintained internally?
How to identify the relative risks and benefits of outsourcing the selected activities? (Quinn, J. B. Hilmer, F. G., 1995).
It has been identified that most managers do not consider the risk factors into account while giving importance only to the costs and benefits of outsourcing and offshoring. Many IT jobs outsourced offshore are help desk jobs. People who hold such jobs typically do not have computing discipline degrees. Murphy and Chabrow (2003) argue that the IT jobs outsourced offshore were the routine, repetitive, and largely uninteresting ones. They are well trained and well versed in the product that they are supporting but in-depth questions regarding the internal workings of the product usually require that a person with a computing discipline degree be summoned to assist. (Antonio M. Lopez, Jr., 2004).
If you need assistance with writing your essay, our professional essay writing service is here to help!
Similar to many other outsourcing projects, the key reason for failure in JIT outsourcing activity is poor management and governance. In order to identify the root cause for this failure, we need to frame the key stages of the outsourcing cycle followed by JIT. Based on the success of Corporate Intranet, selective sourcing was decided. Also, it should be noted that corporate Intranet did not involve any vendor employees and was only purchased and handled completely by the JIT.
IT outsourcing problems usually happen at the contract and post-contract stages (Alborz et al.’s 2003), where how to negotiate and come out with a sound contract, how to manage the contract, and how to build up and maintain a good relationship become the most critical issues IT executives need to face. Managers have to carefully select which IT activities to outsource. John Smith in JIT had an uncertainty about the IT department’s value. In order to resolve the internal Infrastructure department issue, some of the IT activities had been selectively outsourced without a proper strategy. An increased IT costs and poor service level in vendors has been mainly due to ill-defined “relational contracts” and non-flexibility in adapting to both business and technical changes. Thus, many IT activities like JIT did should have remained in-house, but instead were handed over to the vendors.( Lacity, M. C. Willcocks, L. P. Feeny, D. F., 1996).
The IT outsourcing lifecycle suggested by (Sparrow E., 2003) can be used to identify the outsourcing process implemented in the IT department of JIT.
- Initiation
- Vendor Selection
- Contract Negotiation
- Transition
- Service Delivery
- (Continuous)
- Contract Renewal/Termination
- Pre – Execution Execution
- Time
In the Initiation stage, the plan was to outsource the Datacentre management and PC help desk activities to outsourced vendor in order to give provision and for the IT infrastructure group employees to concentrate completely on the enhancement and up gradation of projects within that division. The main motive of outsourcing is generally cost cutting or for maintaining the legacy systems. However, it is required that whatever outsourcing option a company adopts, there is always a need for a capable IS managers to manage the IT operations effectively. It is just not enough to just outsource the work.
A company’s IT managers should also know how to manage contracts and relationships with third parties. The main motives for JIT outsourcing of Datacentre and PC helpdesk were to reduce IT Infrastructure cost, Improve service quality in PC helpdesk and resolve employee retention in the IT infrastructure section. The IT employees were highly qualified and disliked to work on PC helpdesk. There was employee retention in the infrastructure section. The IT employees spent more time on day-to-day maintenance activities due to which they had no time to enhance the existing projects or innovate new ideas for a competitive advantage over other firms.
“A study found that only 54% of the agreements realized expected cost savings (Lacity and Willcocks 1998). More recently, a Gartner Dataquest Report claimed that about one of every three outsourcing contracts targeting cost reductions failed to match expectations (Caldwell 2002b; Caldwell 2002a).”It should also be noted that, when a company outsources its IT services to a third party vendor, how can it be sure that the vendors’ skills would be updated? Moreover, in JIT’s case, cost reduction has been the major concern to decide the outsourcing. Therefore, it cannot expect the vendors CMPI to be updated on technical capabilities and process management. (Earl, M. J., 1996).
In the Vendor Selection, JIT finalized with two vendors for each outsourcing projects. The vendor was mainly selected based on the cost/benefit analysis, expertise level. The Datacentre activities in JIT did not face any cross-cultural issues. However, the PC Helpdesk activity required that the staff should know Japanese language as well, in order to support the rotational staffs. Hence, it is essential that the outsourcing firm should be able to understand and manage the cross-cultural differences. (I Oshri, J Kotlarsky, LP Willcocks, 2009). Among the two vendors that JIT finalised for PC helpdesk outsourcing, ‘CMPI’ was not an experienced company in handling this, whereas, ‘Outsourcing Solutions’ had proposed a unique business model to provide technicians in four different levels covering all aspects including the cross-cultural differences in JIT. The proposal of ‘Outsourcing Solutions’ had to be compromised considering just the cost factor.
The third stage is the Contract Negotiation. In this, JIT had a Service level agreement with both the vendors for a one year contract. Willcocks and Kern (2000) suggest that strategic intent as well as technical capability shape both contract structure and interpersonal relationship development. In JIT’s case, the strategic intent and technical capability of DR solutions was strong. But, it was not the same with CMPI. Thus, it resulted in a very poor interpersonal relationship. Thus, a relationship that aims to tap into the technical leadership capabilities of a vendor to achieve IT efficiency may generate higher value if it is run as a partnership; whereas, one that aims to achieve IT efficiency by tapping into a vendor’s widely available resource pool, may be better managed as a technical supply pay-per-service relationship.
In the transition stage, both the datacentre and helpdesk activities were moved to DR Solutions and CMPI vendor appropriately. The IT manager John Smith did not have a clear cut plan with the outsourcing vendor’s .Immediately after the contract begun; there was not much of monitoring or management of IT operations. (Earl, M. J., 1996). Because of this, it is also likely that the company might have to some of its crucial competencies or capabilities. In JIT’s aspect, there has been value capture of the outsourcing companies but no value creation. Moving the Datacentre from JIT to DR Solutions was not efficient in terms of preplanning. Although JIT had involved 5 different specialists for the deployment, there was no one to actually monitor the process. Moreover, it was not an appropriate time to relocate the Datacentre to the DR Solutions.
In the Service delivery stage, although Datacentre activities was a success, the CMPI employees allocated for PC helpdesk did not possess enough troubleshooting skills right from the beginning, in order to manage the escalation calls they received. They could handle only the quick fixes. They also were reluctant to handle the calls from Japanese executives which clearly convey that, CMPI employees were not well versed in Japanese language. This is another major drawback in CMPI’s business model. Governance is considered not just in terms of pre-specified frameworks for a formal relationship, but that emerge in interactions between client and provider (Mintzberg, 1978). It involves both the client as well as the vendor. The MOG model addresses the question of how a company’s governance affects the outcome of outsourcing in terms of Value Capture and Value Creation. .(Moments of Governance in IS outsourcing: conceptualizing effects of contracts on value capture and creation). Having charged $180/per user/month, the employees felt that they were not receiving a quality service from the PC helpdesk. Thus, John smith decided to improve the quality of service by outsourcing to CMPI and also increasing the user charge $200/month. This did not bring any change in the quality of service. This in turn has increased the expenditure in the Infrastructure division of JIT. Also, there was also a need for expense reduction. Even before finalising the contract with CMPI, John smith had the doubt whether the employees from CMPI would be able to handle the numerous numbers of calls received by JIT per day.
In order to identify the core capabilities of the outsourcing suppliers, the framework proposed by (Feeny, Lacity and Willcocks,2005) can be applied. In this framework, the capabilities of the outsourcing suppliers have been rated based on their Delivery, Relationship and Transformation Competency. Based on the given information, Compared to the Outsourcing Solutions vendor, CMPI had lacked in the leadership, as CMPI had less experience in providing IT services. It had provided services only to 20 companies. Whereas the Outsourcing Solutions vendor had the credit of providing services to Fortune 500 companies. Considering the technical expertise level, CMPI had highly skilled technicians. However, they did not follow any specific business model to implement the helpdesk activities. Whereas, Outsourcing solutions had proposed with a specific business plan with 4 PC helpdesk technicians of 3 different levels for JIT. Also the technicians had excellent resumes and references with them. Also, CMPI were not willing to give an upper limit on the amount of time its employees would take to resolve an escalated call. This information was very unclear when compared to Outsourced solutions. While the Relationship and transformation competency of Outsourced Solutions is much better when compared to CMPI, the cost has been very high. This forced JIT to choose CMPI.(I Oshri, J Kotlarsky, LP Willcocks, 2009).If a company decides to outsource IT services just focusing on costs; It is assuming that its directions and necessities are clear. (Earl, M. J., 1996).
Key Problems with JIT’s Sourcing Strategy:
JIT was focusing more on cost cutting instead of the quality of the service provided by the vendors. This is because, although the vendors CMPI chosen for PC helpdesk activities were not expensive, they did not have as much of experience as the other vendor ‘Outsourced Solutions’. The existing IT division employees at JIT felt that PC help desk Job was not a very productive and was not improving their career as all these employees felt they were overqualified to perform the mundane job. Moreover, as they were spending most of their work hours on maintenance and PC problems, they were unable to concentrate on upgrading or enhancing the existing projects. This eventually started demotivating them.
There was poor governance and Management right from the beginning of the outsourcing contracts initiation. The Service Level agreement was not made clear during the initial contract with CMPI. There have been poor contract and relationship issues. According to Deming (1986), a poor communication or a poor coordination between the vendor and the client is mainly due to poor vendor performance. Some of the anticipated benefits of outsourcing such as cost reduction, expanded, updated skills from vendors and increased flexibility often failed to materialize. (An enterprise perspective of Software Offshoring).Most companies that are outsourcing IT for the first time are not aware of the hidden costs that might start occurring post contract. These may arise as a result of insufficient planning or an unexpected turn of events. (Daniel C. M. Tan, 2009).
The IT director John Smith, who was solely responsible for both the outsourcing projects, did not actually investigate deep into similar outsourcing cases. Based on just the Corporate Intranet outsourcing that gave a success to JIT, he proceeded with this outsourcing decision. He did not give much interest for getting consulting, although he just got a suggestion from one of the known consultants. In Information technology, Customized services are generally not outsourced. As, Michael Cunningham (Ask IT Professional IT Advisory Services Company) Said to John Smith, ‘IT outsourcing is significantly less mature than other outsourcing sectors. Before outsourcing the Datacentre and PC Helpdesk activities, the JIT Company had little knowledge on the Outsourcing strategies. From the client’s perspective, IT outsourcing decision makers are usually short of experience to select and evaluate service providers and immature in negotiating contracts, managing contracts and maintaining good relationships with the providers.(Q.Cong, 2000).
Our academic experts are ready and waiting to assist with any writing project you may have. From simple essay plans, through to full dissertations, you can guarantee we have a service perfectly matched to your needs.
Recommendations for fixing helpdesk problems faced in 2002:
Aron and Singh (2005) suggest that firms should base their outsourcing and offshoring decisions on the assessment of operational and structural risks. For activities that present high operational and structural risks (e.g. corporate planning), they recommend to execute in house and onshore. Activities that present moderate operational and structural risks (e.g. supply chain coordination) they suggest to outsource carefully, using “extended organization” offshore, and monitor closely in real time. Activities with low operational and structural risks (e.g. transaction processing) are suitable for outsourcing to offshore service providers.
With the datacentre outsourcing, although there was a problem in the transition phase, it got resolved immediately due to the vendor’s dedication and strong relationship with JIT. However, there was no risk management planned for both the outsourcing.
With the PC helpdesk outsourcing, rather than choosing the in-house facility, choosing the right vendor/vendors for outsourcing will always be cheaper and efficient for mundane IT tasks. According to Willcocks and Lacity, over 75% of organizations in the developed economies outsource 15%-50% of their IT budgets, typically with multiple suppliers.
JIT can continue for the same SLA with CMPI. But, instead of re-negotiating the contract only with CMPI, it can also involve into a new contract with Outsourced Solutions. As Willcocks (2008) said, “outsource only business and not your problems.” Outsourcing should be viewed as an opportunity and not just as a cost cutting strategy. Hence, JIT should consider the quality, their experience and capability while choosing to outsource the tasks to vendor. As JIT is going to outsource a part of its helpdesk activities to the new vendor, the cost can be reduced. Also through the adoption of multi-vendor strategy, competition between two vendors result in the right pricing for the client and the quality of service will be improved.
In order to resolve the PC helpdesk problem, my recommendation would be to continue with the existing vendor (CMPI) and shift some of the other helpdesk activities to a new vendor. In this case, the new vendor can be ‘Outsourced Solutions’, which means JIT can follow a multi-vendor Outsourcing Strategy. Or, JIT can cancel the contract with CMPI and choose ‘Outsourced Solutions’ for better service.
Benefits / risks of Single vendor Outsourcing strategy:
By adopting a single vendor strategy that JIT already follows, it needs to track only a single implementation. Complexity of management will be much minimized.
This is mainly adopted by clients to benefit from lower operational costs. Similarly, JIT also adopted the single vendor strategy only to lower its operational costs. But, cost should not be the only criteria. Vendor management, capability, and experience, of vendor should be given more importance.
The client can expect the highest level of vendor capabilities through a well-planned Service Level Agreement.
The risks could be poor quality of service by the vendor. There is also a possibility of too much dependency created on the vendor by the client. At the end, this can result in a situation for clients where they cannot move out of the vendor at their will.
However, as JIT failed to follow this strategy efficiently, I would recommend that a multi – vendor offshore outsourcing can be adopted by JIT to solve the issues faced in its Infrastructure section.
Benefits /Risks of Multi-Vendor Outsourcing:
As mentioned earlier, JIT did not follow a risk mitigation methodology while choosing the vendors for both the Datacentre and PC helpdesk activities. Thus when JIT outsources the PC help desk activities to CMPI as well as Outsourced Solutions, it can reduce the risk level because, even when CMPI does not provide a quality service, Outsourced Solutions will be there to backup.
Working with multiple suppliers provides a strong element of power for a company for at least two reasons. First, if a supplier underperforms, it becomes easier to transfer the work to a supplier that is already executing the same processes. Second, working with multiple providers will generate a competitive climate among them that, if managed carefully, can become very beneficial for the customer, both in terms of the quality of service delivered and in terms of price.
As there are two vendors (CMPI and Outsourced Solutions), there is increased domain and technical expertise. This will also enhance the service quality as each vendor will try to compete with the other vendor while providing its services. However, in multi-vendor outsourcing, the companies engage an array of vendors; the managers should be increasingly adept at managing the entire portfolio of vendors. Thus, John Smith should think beyond cost to ensure the success of the PC helpdesk outsourcing. (Lacity, M., Willcocks, L. and Feeny, D., 1996).
Firstly, vendor’s familiarity with the business is most important. Although, CMPI was familiar with helpdesk activities, it was not aware of the actual activities happening in the Infrastructure section in JIT. (Kakabadse, A., and Kakabadse, N., 2000) Secondly, there should be good involvement from the JIT’s IT team to equally co-operate with the vendor’s employees. (Kreitner, R. and Kinicki, A., 2007).

Word Processing is a computer application which allows a document to be created, edited, stored and printed. By clicking within any document with your mouse you can add or delete content and graphics.
There are several different types of Word processing programs. Microsoft Word is one of the most popular and frequently used applications. It is generally the best package to buy because it is part of Microsoft Office Suite, which includes PowerPoint and Excel; it is also cost effective and is easy and practical to use. [2]
Text Manipulation is being able to change the appearance of the text in a word document using the Font Icons. These icons are; fonts, size, font styles and enhancement (such as colour). These changes can be done by highlighting specific text, whole paragraphs or the entire document and clicking on the appropriate icon in the tool bar. [3]
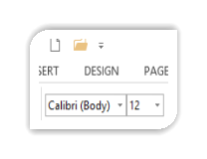 Work Processing has a default writing style and size.
Work Processing has a default writing style and size.
In order to change either of these, click on the down arrow and different fonts will appear. Select the font desired.
 To the right of the font box, the size of the font can be selected and changed by using the down arrow and selecting the size suitable for the document you are working on. Sizes 10 and 12 are the most commonly used for letters and documents and larger sizes are used for headings.[4]
To the right of the font box, the size of the font can be selected and changed by using the down arrow and selecting the size suitable for the document you are working on. Sizes 10 and 12 are the most commonly used for letters and documents and larger sizes are used for headings.[4]



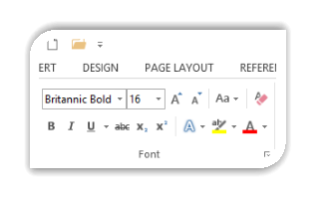 The Font styles found in the toolbar are Italic, Bold, Underline, Strikethrough, Superscript and Subscript. Text effects, Highlight and font colour are also here.
The Font styles found in the toolbar are Italic, Bold, Underline, Strikethrough, Superscript and Subscript. Text effects, Highlight and font colour are also here.
 BOLD style can be applied by selecting the text to appear in bold and pressing the ‘B’ button. Similarly, using the italics and underline button can change the appearance of the text. Colour can also be found here and used to enhance the appearance of the document.
BOLD style can be applied by selecting the text to appear in bold and pressing the ‘B’ button. Similarly, using the italics and underline button can change the appearance of the text. Colour can also be found here and used to enhance the appearance of the document.
Formatting a document is the layout of a document. There are several applications that can help in doing this.
- Alignment
- Margins
- Spacing
- Indenting
- Layout
- Borders
- Headers & Footers
The Alignment of text in a document shows where the text sits in that document. Text can be aligned in several different ways.
- Left Alignment: This the default position in word processing where the text is lined up with the left edge of the page. It is often used for the date and address on letters.
- Right Alignment: the text is lined up with the right edge of the page. This can also be used for addressing letters.
- Centre Alignment: the text is placed in the middle of the document. This is used for headings, where centering is required.
- Justification Alignment: text is lined up with both left and right hand edges of the page. This layout is seen in newspapers.[5]
 To use Alignment on text, highlight the section to be aligned. To highlight the full document use Ctrl + A. Then click on the Home page; go to the Paragraph box and click on the alignment needed.[6]
To use Alignment on text, highlight the section to be aligned. To highlight the full document use Ctrl + A. Then click on the Home page; go to the Paragraph box and click on the alignment needed.[6]
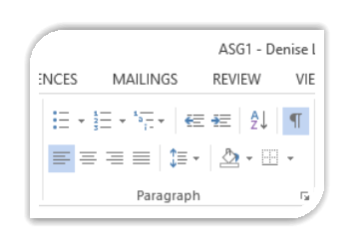

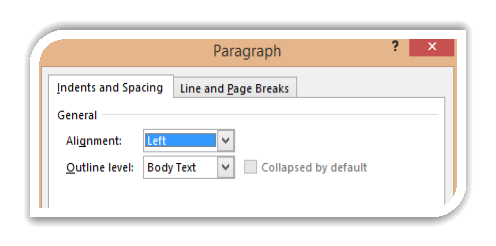
 Using the arrow on the right hand corner of the paragraph box, alignment can be set manually also.
Using the arrow on the right hand corner of the paragraph box, alignment can be set manually also.
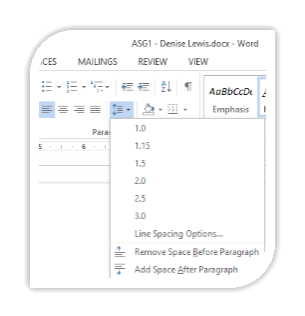 Line spacing in Word Processing can be set as a single space between lines of text in a paragraph, to any appropriate space needed. The default space setting is 1.15, which makes text more readable.
Line spacing in Word Processing can be set as a single space between lines of text in a paragraph, to any appropriate space needed. The default space setting is 1.15, which makes text more readable.
 Go to Home in address bar.
Go to Home in address bar.- Click on the downward arrow.
- A list of options allows a line spacing
value to be chosen.
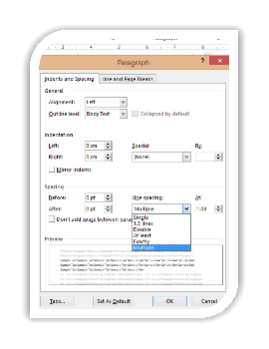 Specific spacing options can be chosen.
Specific spacing options can be chosen.
 Click on the downward arrow in the corner of the Paragraph box.
Click on the downward arrow in the corner of the Paragraph box.- The menu allows specific line-spacing values to be set from the Spacing area of the menu.
 The Multiple Line Spacing menu, along with At, allows spacing to be customised.
The Multiple Line Spacing menu, along with At, allows spacing to be customised.
Click ok when values are chosen.[7]

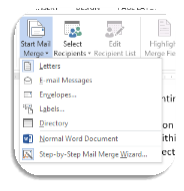 Go to Mailings in the ribbon bar.
Go to Mailings in the ribbon bar.- Click on the Start Mail Merge arrow.
- Select ‘Labels’ from the drop-down menu.
- Within the application that opens, choose the appropriate sized label and click ok.
- The label selected will appear in box.
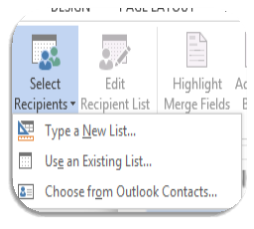
Go to Select Recipients and select from the drop-down menu that appears.
 Click on the appropriate line.
Click on the appropriate line.- This will link both labels and addresses.
- Ensure cursor is present in the first cell.
 Click on Insert Merge Field and insert each line of address.
Click on Insert Merge Field and insert each line of address.- Click on Update Labels and this address will appear in each cell.
 Click on Preview Results to check addresses are correctly placed.
Click on Preview Results to check addresses are correctly placed.
 To change the alignment of address, highlight all the cells; go to Tools Bar;
To change the alignment of address, highlight all the cells; go to Tools Bar;
click on Layout and choose appropriate
alignment.
- Click on Finish & Merge icon.[8]
Tabs are used for lining up text.
- Set by placing the cursor on the ruler bar across the top of the page.
- Click at each point on the lower line where a tab is needed.
- The pre-set tabs will disappear and the tabs needed for the document are left.
- When the tab key is pressed, the cursor will move to the next tab point.[9]
Tab stops can be set precisely to customise a document by using the Tabs dialog box.
- Go to Page Layout
- Click on the corner downward arrow in the Paragraph box.
 In the dropdown Menu, click on Tabs button.
In the dropdown Menu, click on Tabs button.

 Set parameters in the Tab box:
Set parameters in the Tab box:
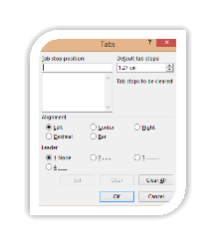 In Tab stop position, select location of Tab.
In Tab stop position, select location of Tab.- In Alignment, select type of Tab stop.
- In Leader box select type needed.
- Click Set.
Graphics is the display and manipulation of pictures in Word Processing. Word Processing allows pictures to be drawn or imported from several different sources; e.g., Online pictures, personal photos stored on the computer, Clipart, SmartArt, and Screenshots.
Graphics are used to support text, to make it more interesting and to enliven the document.[10]
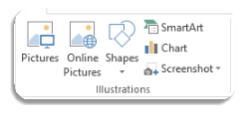 Go to INSERT on the address bar.
Go to INSERT on the address bar. In the Illustrations box, graphics can be accessed from the different sources.
In the Illustrations box, graphics can be accessed from the different sources.

To Access graphics from the Internet
- Go to Illustrations.
- Click on Online Pictures.
- Type in Search box required image.
 Select image and click Insert.
Select image and click Insert.
Tables in Word Processing are made-up of rows and columns. They are easy to create and using tables in Word Processing is made easy by the variety of features present which allows the user to present professional looking tables.[12]
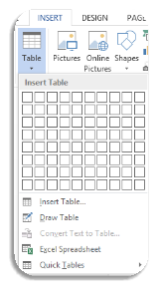
Creating a Table
- Place your cursor where you want
the table to be.
- Go to INSERT in the address column.
- Click on downward arrow in Table box.
 Click on Insert Table
Click on Insert Table
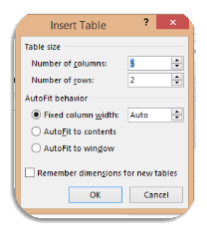
 Insert Table dialog box appears
Insert Table dialog box appears- Put in parameters required
- Click ok.
- Table now appears in document[13]
To increase the number of cells, rows and columns can be done with the click of a button.
To add a row to a Table place your cursor in the cell above where you want the row to appear.
- Go to Table Tools
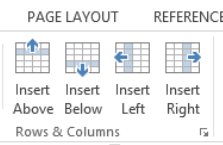 click on Layout
click on Layout Click on Insert below
Click on Insert below
To add a column, place the cursor in the column beside which you the column to appear.
- Go to Table Tools
- Click on Layout
- Click on Insert Right or Insert Left[14]
File Handling and File Management
File management and Handling is how data is organised on a computer system. By naming, storing and handling files logically, they can be retrieved easily and conveniently.[15]
There are several functions in file management /handling that allow creating, deleting and maintaining files.[16]
Folders
Save
Save As
File Type; e.g. Word 2010, PDF
Folders
To create a folder
- Right click on the desktop
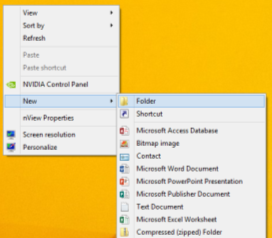 Click on New in the dropdown menu
Click on New in the dropdown menu- Name Folder
Each Folder has a unique name. Sub folders can be create within a folder. Files are stored within folders.
Save & Save As
 The Save button is used when you are making changes to an existing document and you want to save the changes you make.
The Save button is used when you are making changes to an existing document and you want to save the changes you make.
Save As is used when you have saving information into a file.
[1] https://tepfenhart506.wordpress.com/lesson-plan/ – accessed 28/09/16
[2] http://techterms.com/definition/wordprocessor
[3] Creative Training, Word Processing QQI level 5 – accessed 29/09/16
[4] http://www.nuim.ie/staff/dpringle/gis/HDip/hdgis04.pdf – accessed 30/09/16
5 Creative Training, Word Processing, QQ1 Level 5 – accessed 30/09/16
[5] Creative Training, Word Processing, QQI Level 5 – accessed 04/10/2016
[6] https://support.office.com/en-ie/article/Format-a-document-in-Word-2016-780772c6-9506-4081-afd1-aff9aab19f5f
[7] Creative Training, Word Processing, QQI Level – accessed 06/10/16
[8] Creative Training, Word Processing, QQI Level 5 – accessed 05/10/16
[9] www.compukiss.com/tutorials/word-processing-basic-terminology.html – accessed 05/10/16
[10] http://howtogeek.com/school/microsoft-word – accessed 05/10/16
[11] http://year9top10.wikispaces.com/top+ten+web+pages
[12] http://www.teach-ict.com/gcse_new/software/word_processor/miniweb/pg14.htm – accessed 06/10/16
[13] Creative Training, Word Processing, QQI Level 5 – accessed 06/10/16
[14] Creative Training, Word Processing, QQI Level 5 – accessed 07/10/16

 Analysis Of Word Processing Programmes
Analysis Of Word Processing Programmes